We can use Managed Identities when managing apps created in Azure. Instead of using Entra ID Application Identities and having to store and secure the client secret of the app, Microsoft will take care of it.
Identity for a solution that is running in Azure, a virtual machine, app service, function apps.
Types of Managed Identity
System assigned
Managed identity for a single resource Will be erased when resource is destroyed
User assigned
A user can create and share an identity with multiple resources Will not be erased along with resource
Enabling a System Assigned Managed Identity
Under a virtual machine or any other resource, navigate to Identity Toggle the status to ‘On’ and Save:
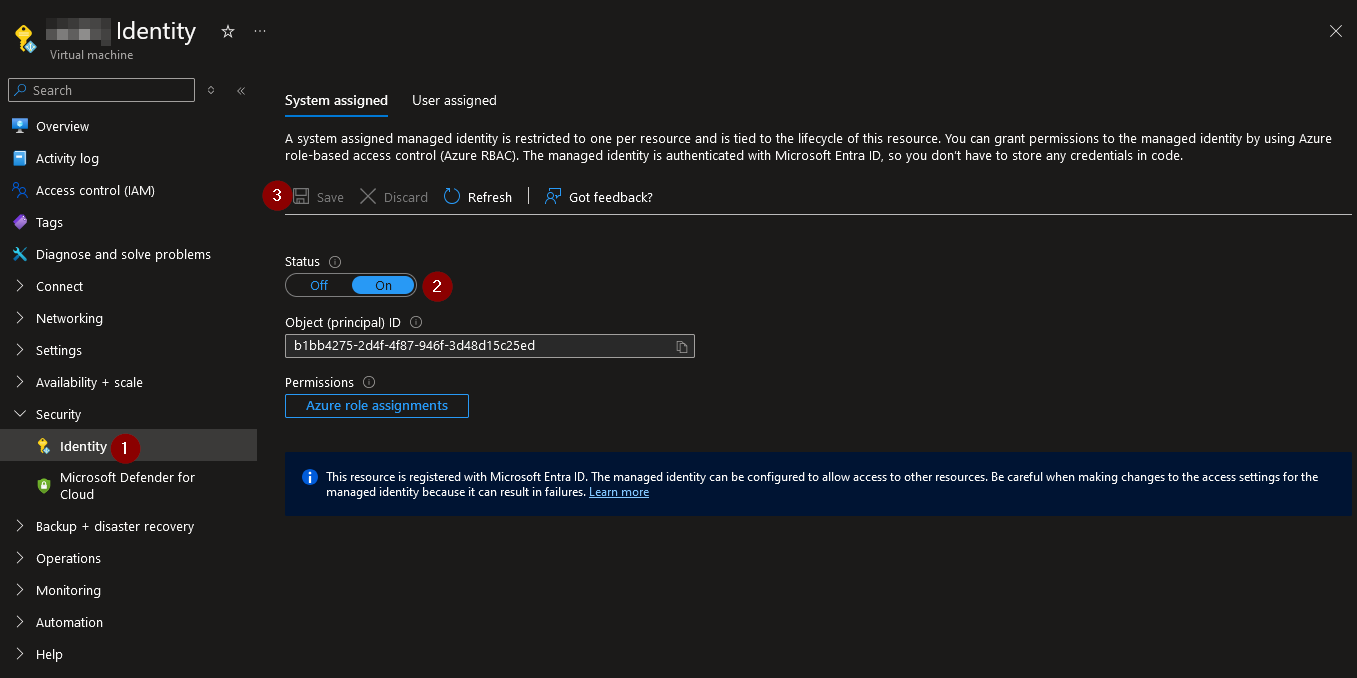
Now that we have enabled a managed identity, we can now assign a role to the identity.
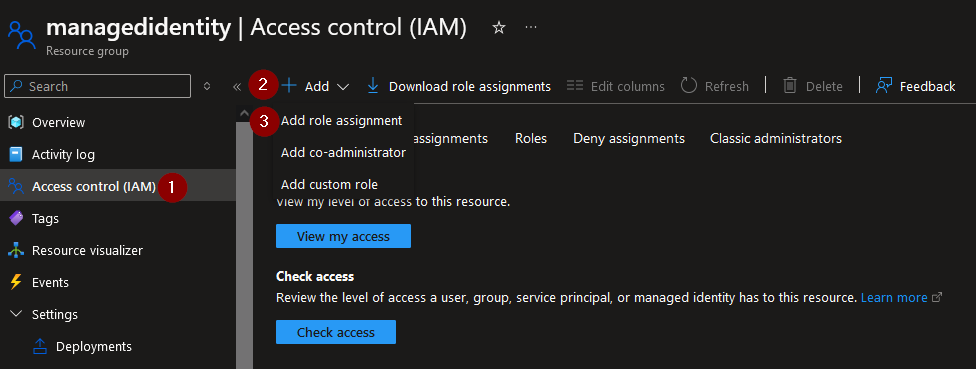
Navigate to the resource group the virtual machine is at and add a role assignment:
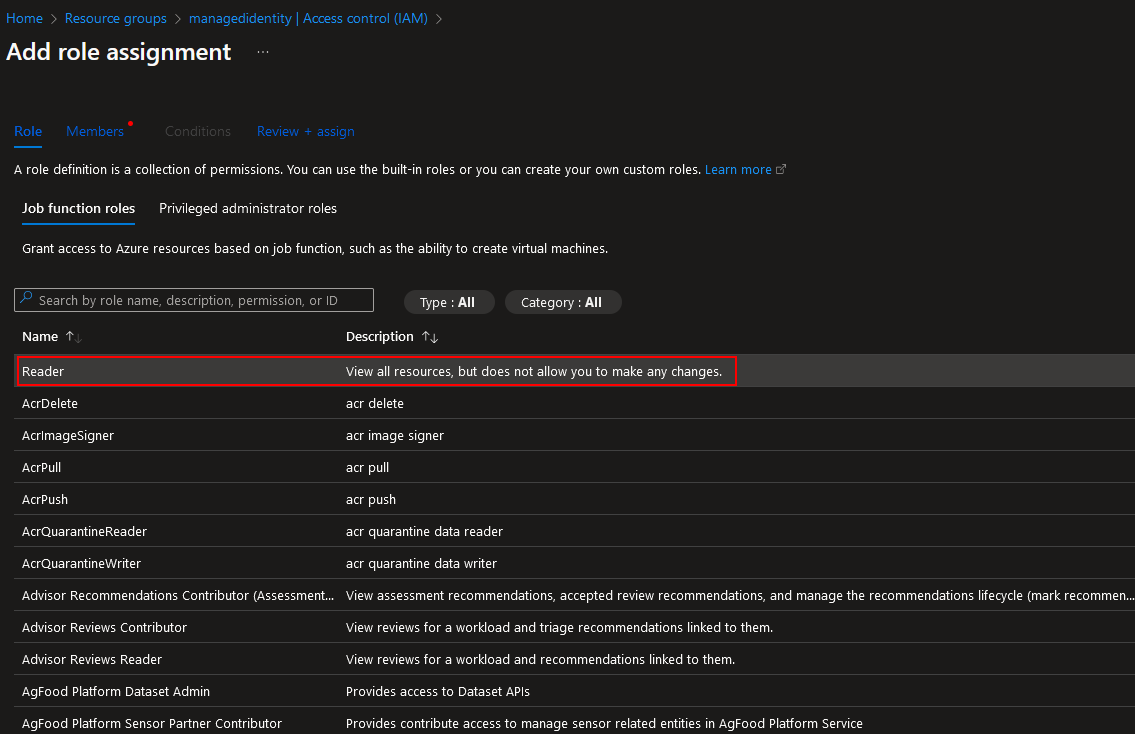
Select the ‘Reader’ role:
Select Managed identity and add the virtual machine, review and assign:
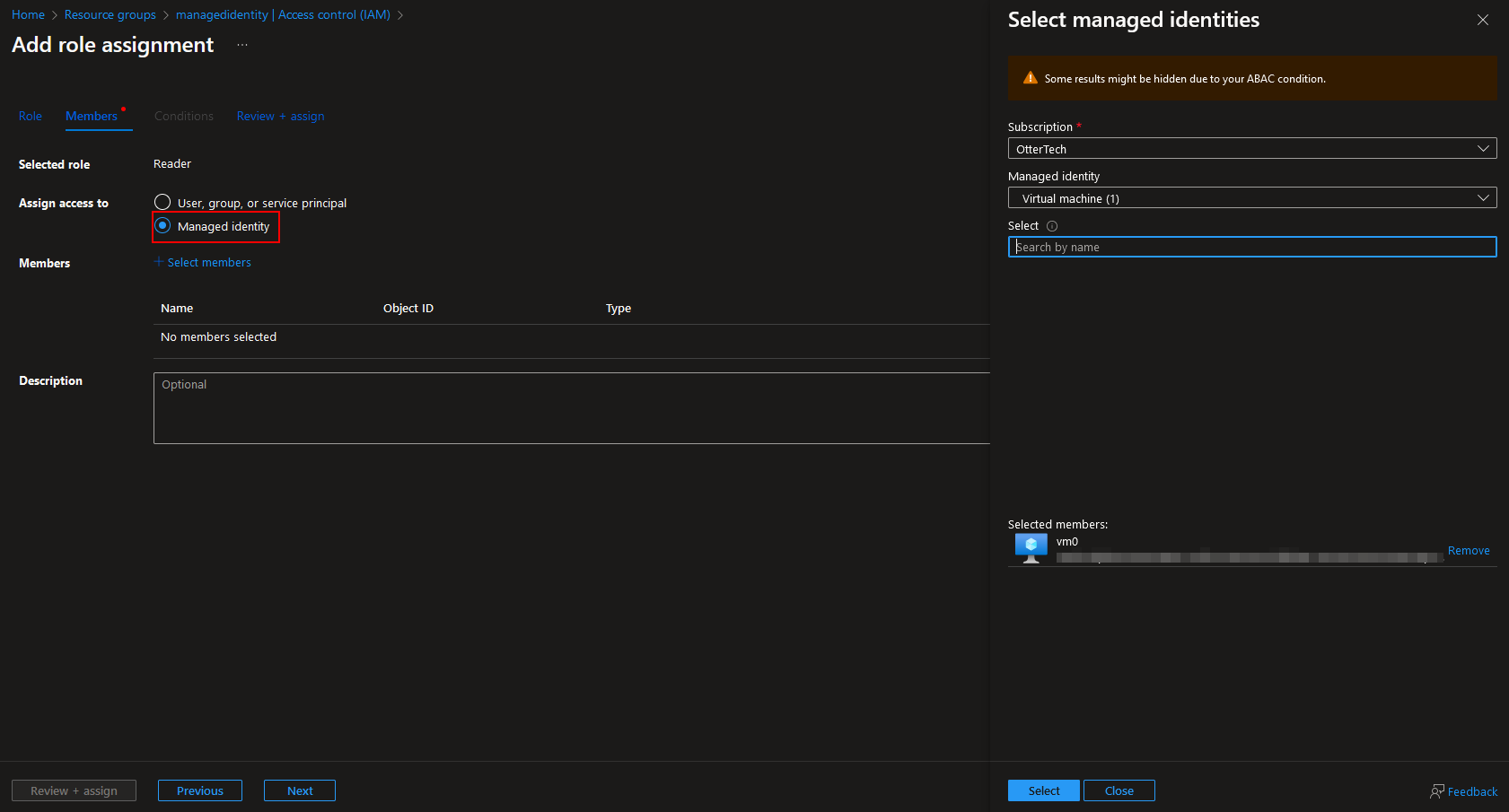
We have added roles to the identity.
Logging in as the Managed Identity
In a virtual machine, open PowerShell as Admin:
az login --identity
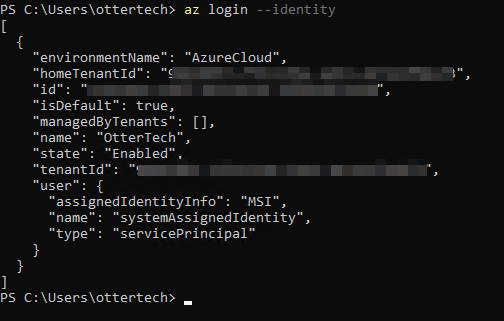
We have now logged in as the Microsoft system assigned managed identity.
Creating a User Assigned Managed Identity
Navigate to the Managed Identities and select ‘Create’:
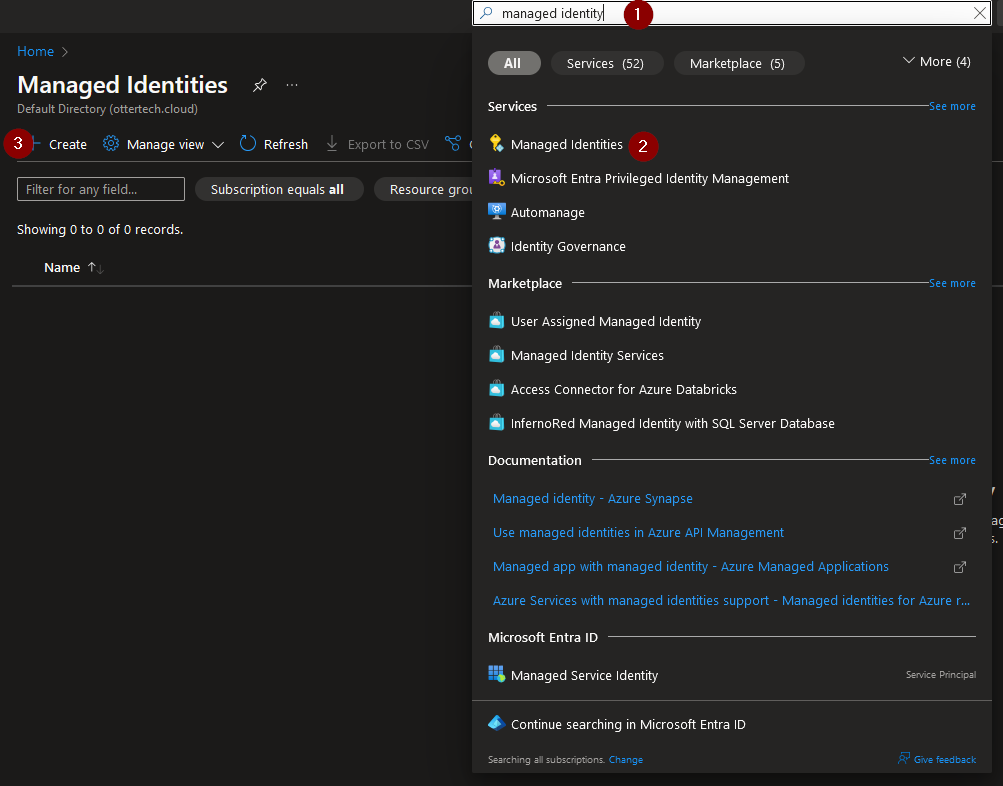
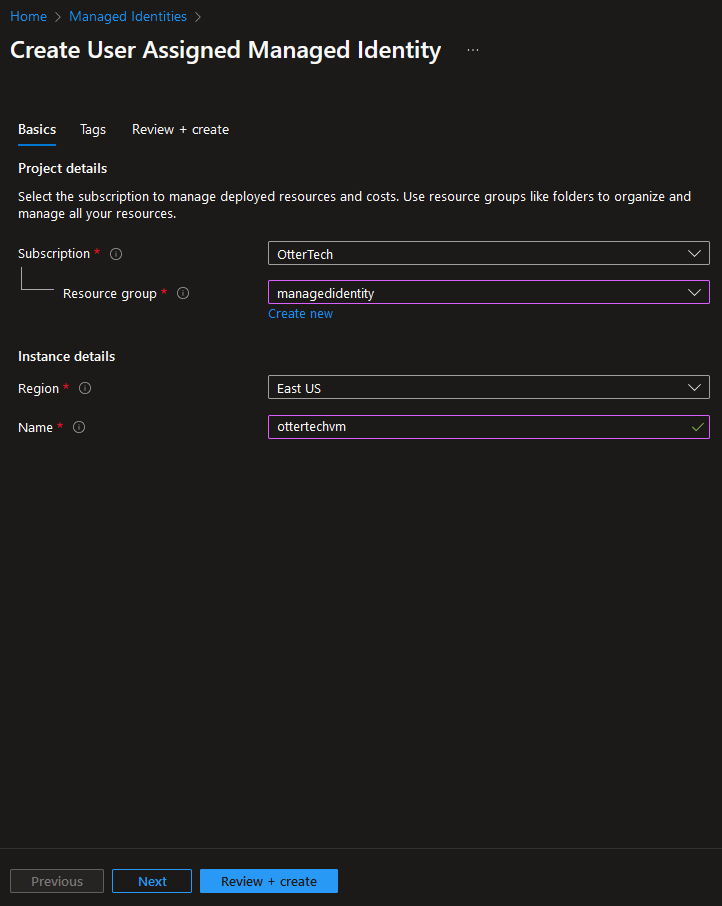
Select the resource group and give the instance (managed identity) a name:
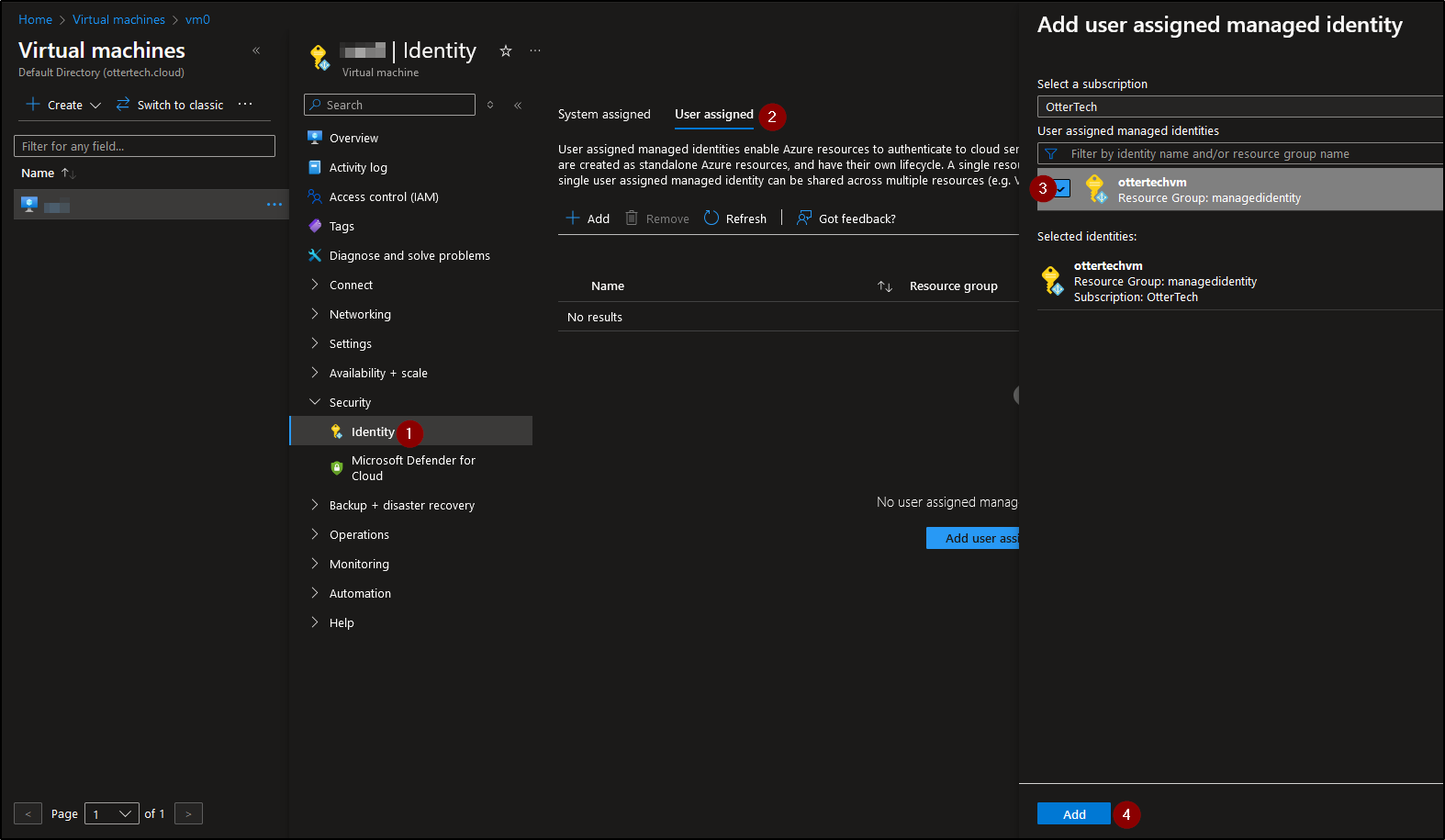
We can go to multiple virtual machines and assign the User assigned identity:
Note
You will need to assign the proper RBAC roles to the User assigned Identity in the Subscription level.
We have now assigned a user assigned managed identity to a resource.