In order to implement conditional access policies, we need to disable the default ones put in place by Azure.
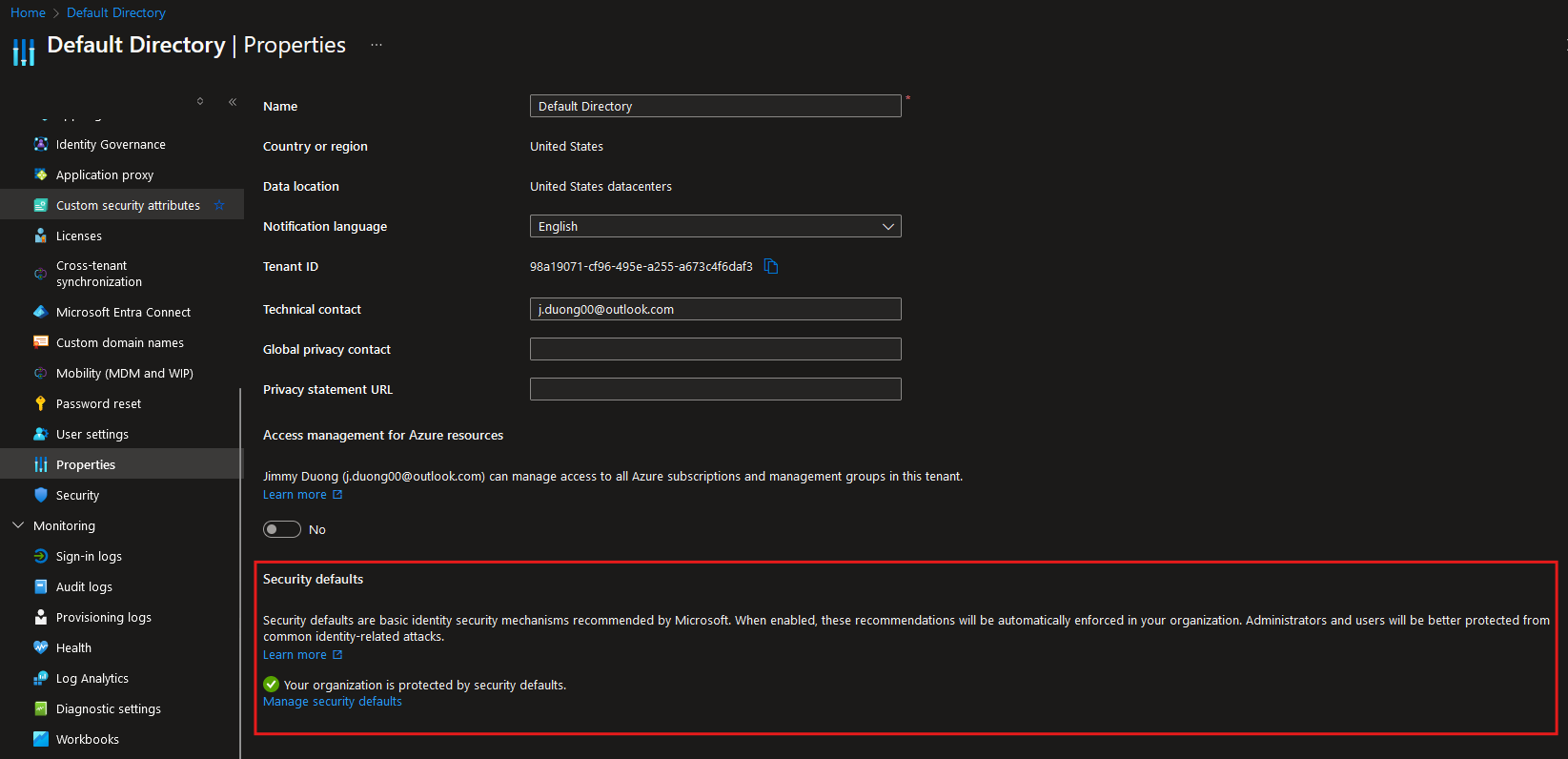
Navigate to Entra ID, under Properties select ‘Manage security defaults’:
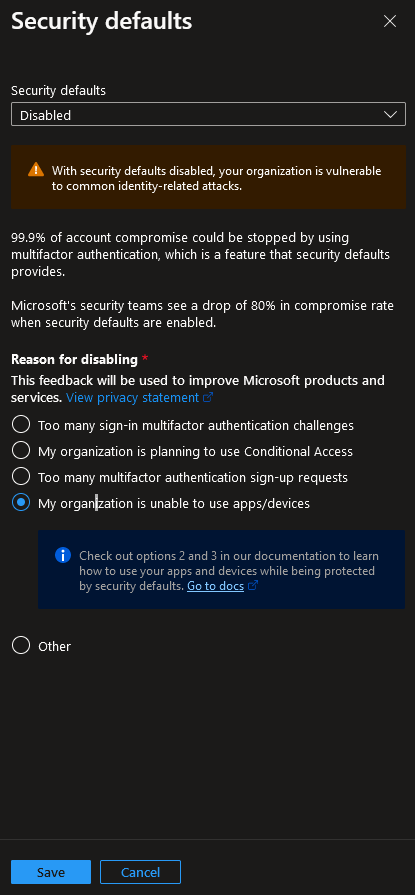
In the ‘Security defaults’ choose the ‘Disabled’ option in the dropdown and click save:
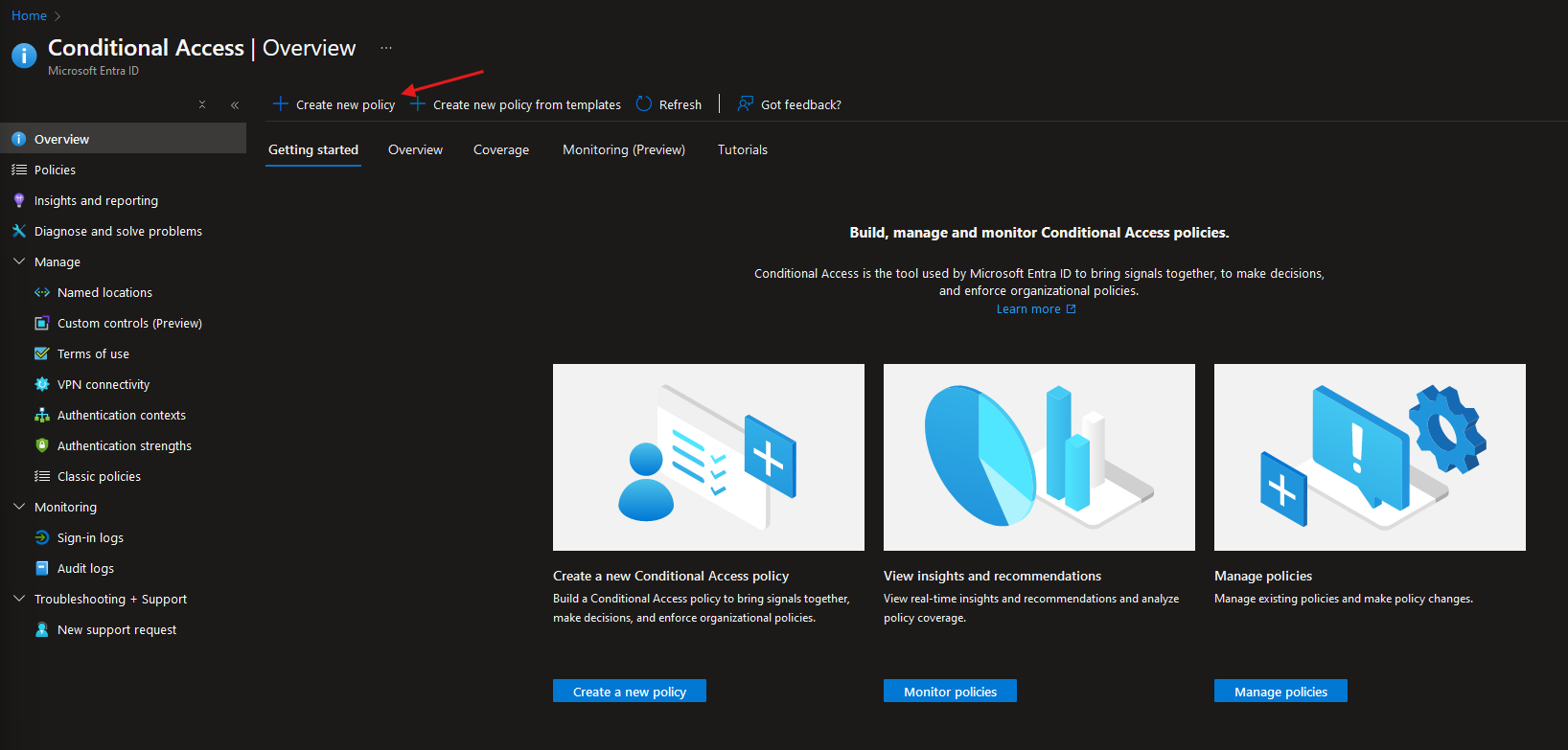
In Entra ID, select ‘Create new policy’:
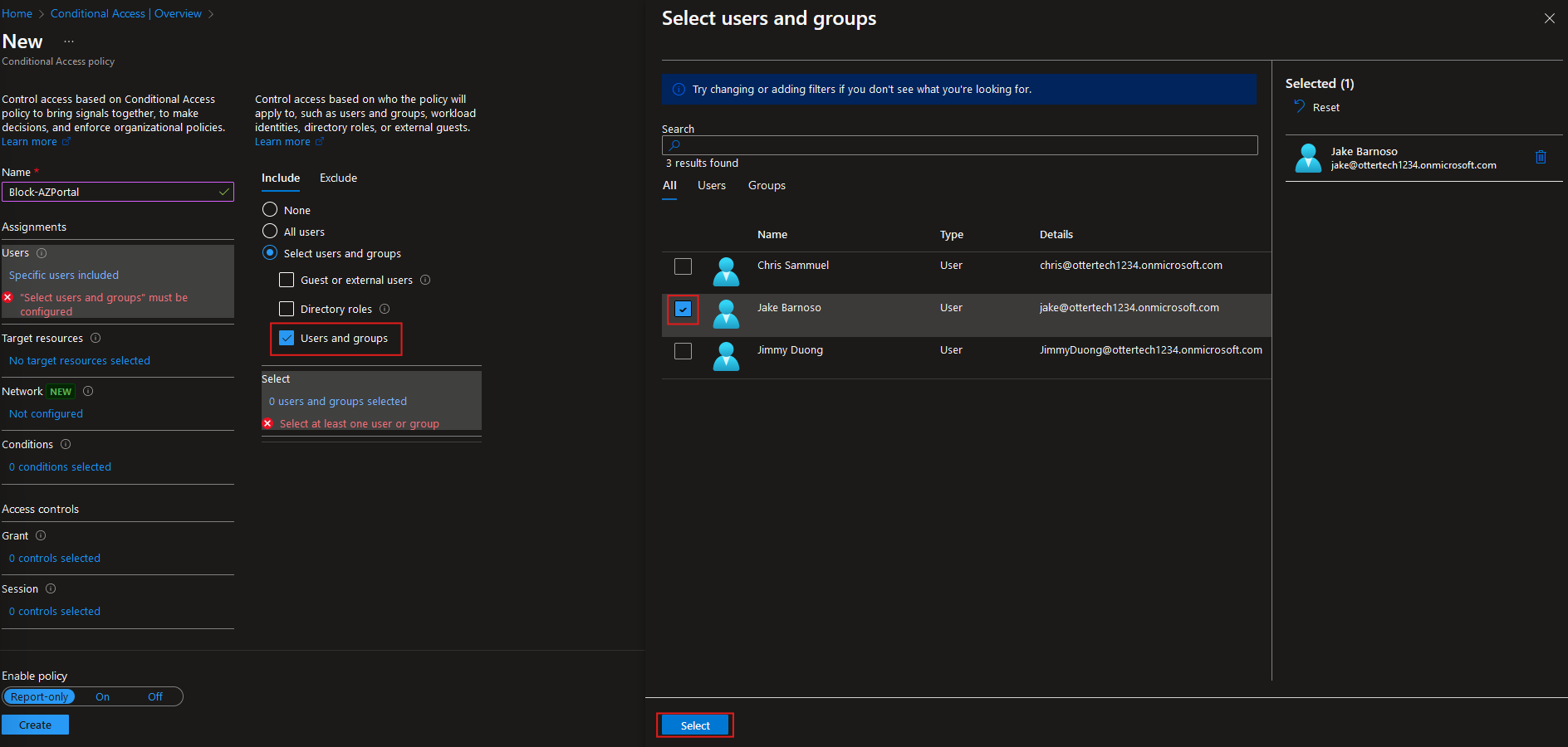
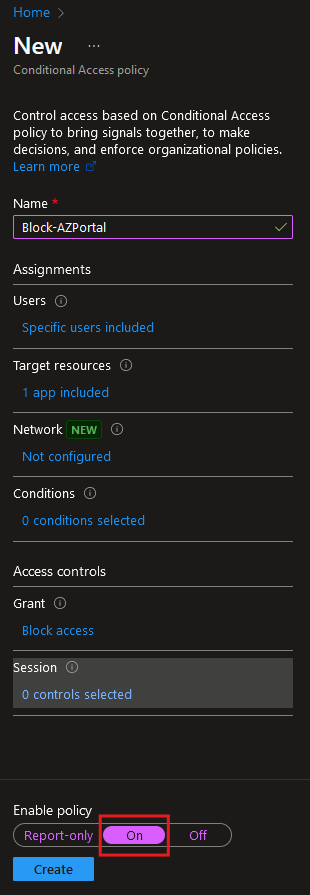
Give the policy a name and select the scope of the policy, here we are blocking user access to the Azure portal:
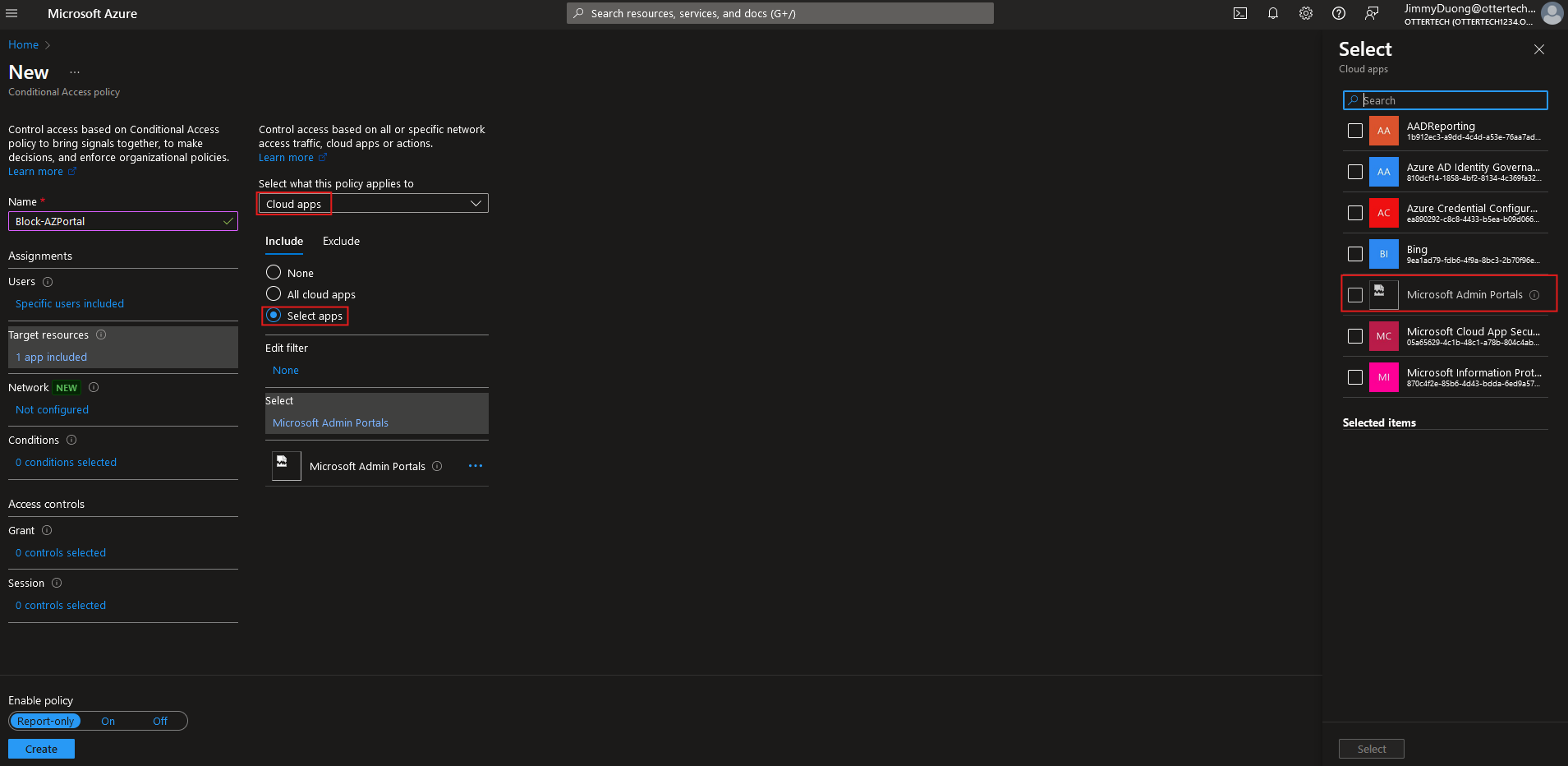
In the ‘Target resources’ section, select ‘Cloud apps’, and select ‘Microsoft Admin Portals’. This will block access to Microsoft 365 admin center, Exchange admin center, Azure portal, Microsoft Entra admin center:
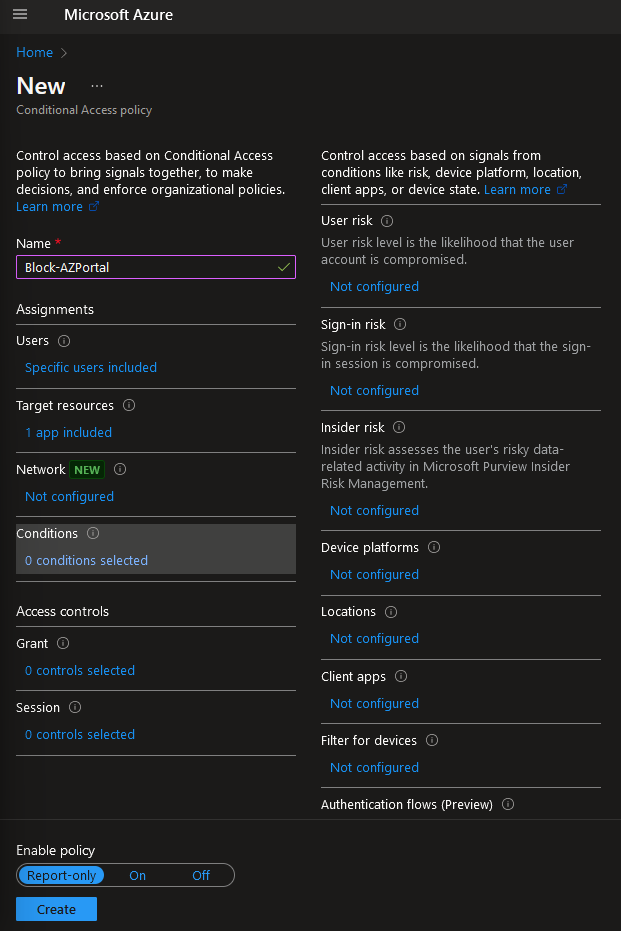
In the Conditions, we can configure access based on signals such as location and device state. For this demonstration, we will totally block access so we will not configure anything here:
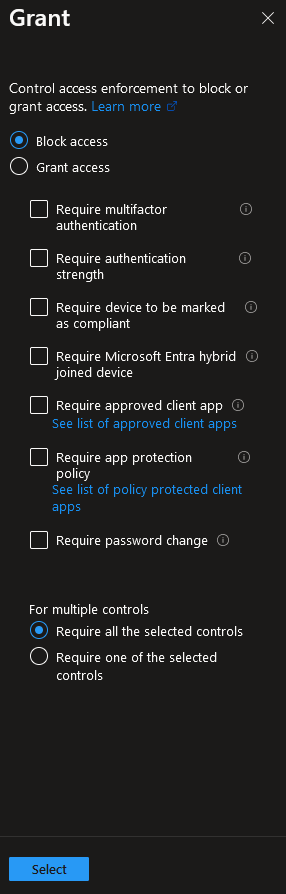
In the Grant section, select ‘Block access’ as we are completely blocking access for the user. Instead, we can allow access depending on various factors:
Turn on the ‘Enable policy’ and click Create:
The user is now blocked from accessing the Azure portal.
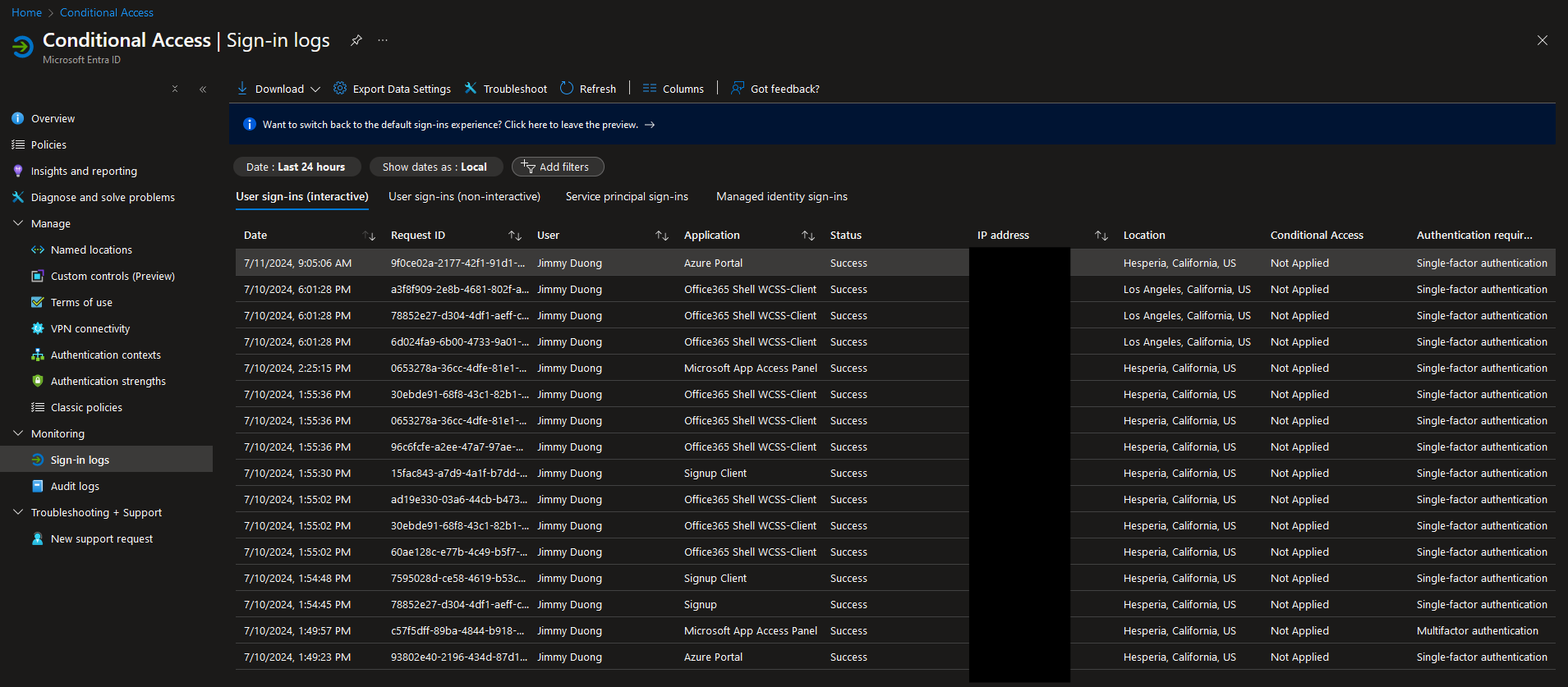
Checking Sign in Logs
To check the sign in logs, navigate to Entra ID > Conditional Access > Monitoring > Sign in logs. Here we can see the user that signed in, the application and various other datapoints such as date and access location.